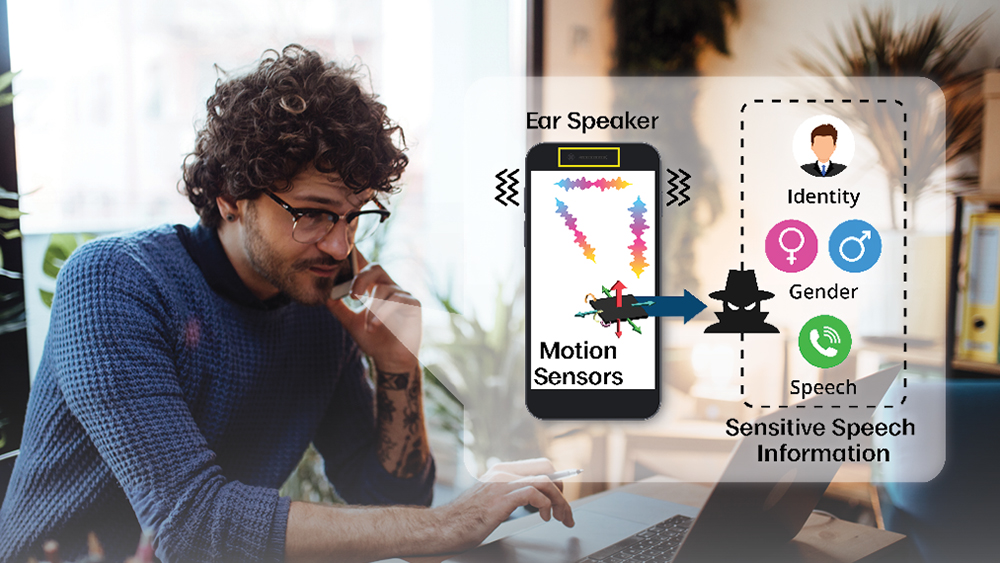
Male hacker uses the mobile phone to hack the system. Concept of cyber crime and hacking electronic devices Photos | Adobe Stock

Who's Calling? Gaza and West-Bank Hackers Exploit and Monetize Corporate VoIP Phone System Vulnerability Internationally - Check Point Blog

Hacking des téléphones mobiles : les techniques les plus récentes et les plus couramment utilisées par les pirates informatiques - IT SOCIAL

.jpg)













/Hacked-phone-02.png?width=1319&name=Hacked-phone-02.png)